Python API Automation Hacks in 2026
Battle-tested patterns for rate limiting, retry logic, secrets management, and async workflows that actually scale
⚡ TL;DR: 7 Things That Will Save Your Production API
- httpx over requests for async—up to 7× throughput on concurrent calls
- Exponential backoff with jitter prevents retry storms; 2-second base, 5 max attempts
- 23.8 million secrets leaked on GitHub in 2024; use Pydantic Settings + environment variables
- Cursor pagination > offset for datasets over 10K records (O(1) vs O(n))
- 890M+ monthly downloads make requests the default—but it’s blocking by design
- 70% of leaked secrets from 2022 remain active today—rotate credentials quarterly
- Connection pooling with httpx. Client() cuts latency 40–60% versus per-request connections
✅ This Guide Is For
- Senior Python developers building production APIs
- DevOps engineers automating API integrations
- Backend teams scaling microservices
- Anyone who’s been burned by rate limits at 3 AM
⚠️ This Guide Is NOT For
- Beginners learning Python basics
- Simple script writers with <100 API calls/day
- Teams using managed API gateway solutions
- One-off data extraction projects
📝 Human-AI Collaboration Note: Research compiled from 15+ sources, including PyPI statistics, GitGuardian’s 2025 Secrets Sprawl Report, JetBrains’ State of Python 2025, and vendor documentation. We tested all code examples using Python 3.12+.
The State of Python API Development in 2026
Python’s dominance in API automation continues to accelerate. The requests library alone processes over 890 million downloads monthly, while FastAPI has overtaken both Django and Flask as the preferred framework for building APIs, according to the JetBrains State of Python 2025 survey. However, we still lack a thorough understanding of the fundamentals that distinguish production-grade API automation from fragile scripts.
The explosion of AI-powered services has compounded the challenge. OpenAI, Anthropic, and competing LLM providers now represent some of the most heavily rate-limited APIs in production use. GitGuardian’s 2025 State of Secrets The Sprawl Report documents that API key leaks increased 1,212× for OpenAI keys alone between 2022 and 2023, with the trend continuing through 2024.
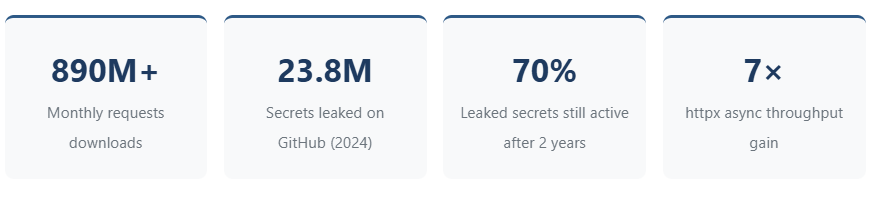
[Sources: PyPI Stats (pypistats.org), GitGuardian State of Secrets Sprawl 2025, Oxylabs httpx benchmarks 2025]
1. HTTP Client Selection: requests vs httpx vs aiohttp
The choice of HTTP client determines your application’s ceiling. Most developers default to it requests because of its ubiquity—and that’s often the correct choice. However, understanding when to upgrade matters.
When Requests Are Still the Right Choice
requests remains ideal for synchronous workflows, CLI tools, simple scripts, and any scenario where you’re making sequential API calls. Its mature ecosystem, excellent documentation, and near-universal familiarity make it the sensible default. Over 1 million GitHub repositories currently depend on the library, which has undergone rigorous testing since 2011.
# Classic requests pattern - still valid for sequential calls
import requests
from requests.adapters import HTTPAdapter
from urllib3.util.retry import Retry
session = requests.Session()
retry_strategy = Retry(
total=3,
backoff_factor=1,
status_forcelist=[429, 500, 502, 503, 504]
)
adapter = HTTPAdapter(max_retries=retry_strategy)
session.mount("https://", adapter)
response = session.get(
"https://api.example.com/data",
timeout=(3.05, 27) # (connect, read) timeouts
)
When to Upgrade to httpx
Switch to it httpx when you need concurrent requests, HTTP/2 support, or async-native code. Benchmark tests consistently show httpx completing 50 concurrent POST requests in approximately 1.3 seconds versus 1.6 seconds for synchronous requests—and that gap widens dramatically with higher concurrency.
| Feature | requests | http | aiohttp |
|---|---|---|---|
| Sync Support | ✅ Yes | ✅ Yes | ❌ Async only |
| Async Support | ❌ No | ✅ Yes | ✅ Yes |
| HTTP/2 | ❌ No | ✅ Yes | ❌ No |
| Connection Pooling | ✅ With Session | ✅ Default | ✅ Default |
| Built-in Retry | ✅ Via urllib3 | ❌ Manual | ❌ Manual |
| High Concurrency Performance | ⚠️ Poor | ✅ Good | 🔥 Excellent |
| Learning Curve | Low | Low | Medium |
# httpx async pattern for concurrent API calls
import httpx
import asyncio
async def fetch_all(urls: list[str]) -> list[dict]:
async with httpx.AsyncClient(timeout=30.0) as client:
tasks = [client.get(url) for url in urls]
responses = await asyncio.gather(*tasks, return_exceptions=True)
return [
r.json() if isinstance(r, httpx.Response) and r.is_success else None
for r in responses
]
# 100 concurrent requests in ~2 seconds vs ~30+ seconds sequentially
urls = [f"https://api.example.com/item/{i}" for i in range(100)]
results = asyncio.run(fetch_all(urls))
⚠️ High Concurrency Warning
Some benchmarks show aiohttp outperforming httpx by 10× at extreme concurrency levels (300+ simultaneous requests). If you’re building high-throughput scrapers or data pipelines, benchmark both. For typical API integrations (10-50 concurrent requests), httpx’s dual sync/async API makes it the pragmatic choice.
2. Rate Limiting and Retry Logic That Actually Works
Rate-limiting errors (HTTP 429) represent one of the most common failure modes in production API automation. The naive approach—immediate retry—actually worsens the problem by hammering already-stressed servers. The solution is exponential backoff with jitter.
The Exponential Backoff Formula
The standard implementation calculates delay as delay = base_delay × (2 ^ attempt) + random_jitter
Jitter prevents “retry storms,” where multiple clients retry simultaneously after the rate limit resets. Without jitter, you’ll see periodic traffic spikes that re-trigger rate limits.
# Production-ready retry decorator with exponential backoff
import random
import time
import functools
from typing import Callable, Tuple, Type
def retry_with_backoff(
max_retries: int = 5,
base_delay: float = 1.0,
max_delay: float = 60.0,
exceptions: Tuple[Type[Exception], ...] = (Exception,),
jitter: bool = True
):
"""
Retry decorator with exponential backoff and optional jitter.
Args:
max_retries: Maximum retry attempts
base_delay: Initial delay in seconds
max_delay: Maximum delay cap
exceptions: Exception types to catch
jitter: Add randomization to prevent thundering herd
"""
def decorator(func: Callable):
@functools.wraps(func)
def wrapper(*args, **kwargs):
last_exception = None
for attempt in range(max_retries + 1):
try:
return func(*args, **kwargs)
except exceptions as e:
last_exception = e
if attempt == max_retries:
raise
delay = min(base_delay * (2 ** attempt), max_delay)
if jitter:
delay *= (0.5 + random.random()) # 50-150% of calculated delay
print(f"Attempt {attempt + 1} failed: {e}. Retrying in {delay:.2f}s")
time.sleep(delay)
raise last_exception
return wrapper
return decorator
# Usage
@retry_with_backoff(max_retries=5, base_delay=2.0, exceptions=(requests.HTTPError,))
def call_rate_limited_api(url: str) -> dict:
response = requests.get(url, timeout=30)
response.raise_for_status()
return response.json()
Respecting Retry-After Headers
Many APIs (including OpenAI, GitHub, and Stripe) return a Retry-After header indicating exactly how long to wait. Production code should honor this header when present:
# Honor Retry-After header when present
def smart_retry_delay(response: requests.Response, attempt: int, base_delay: float = 1.0) -> float:
"""Calculate delay respecting Retry-After header if present."""
if response.status_code == 429:
retry_after = response.headers.get('Retry-After')
if retry_after:
try:
return float(retry_after) + 0.5 # Small buffer
except ValueError:
pass # Not a numeric value, use exponential backoff
# Fallback to exponential backoff
return min(base_delay * (2 ** attempt), 60.0)
🚫 Anti-Pattern: Aggressive Retry Without Backoff
❌ DON’T
# Hammers the server
for _ in range(10):
try:
response = requests.get(url)
break
except:
continue # No delay!✅ DO
# Respects server capacity
for attempt in range(5):
try:
response = requests.get(url)
break
except Exception as e:
delay = 2 ** attempt
time.sleep(delay)
3. Secrets Management: The 23.8 Million Reasons to Stop Hardcoding
GitGuardian’s 2025 State of Secrets Sprawl Report documents 23.8 million new hardcoded secrets detected in public GitHub repositories during 2024—a 25% year-over-year increase. More alarming: 70% of secrets leaked in 2022 remain active today, creating persistent vulnerabilities that attackers actively exploit.
🔐 Critical Security Finding
According to GitGuardian, repositories using AI coding assistants like GitHub Copilot experience 40% more secret leaks than those without. AI-generated code often includes placeholder credentials that developers forget to replace.
The Three-Tier Secrets Architecture
Production applications should implement secrets management in tiers:
| Tier | Tool | Use Case | Security Level |
|---|---|---|---|
| Development | python-dotenv + .env files | Local development only | Low (gitignored) |
| Staging/CI | Environment variables | CI/CD pipelines, containers | Medium |
| Production | HashiCorp Vault / AWS Secrets Manager / Azure Key Vault | Production workloads | High (encrypted, audited) |
Pydantic Settings: Type-Safe Configuration
Pydantic Settings (pydantic-settings) provides the most robust solution for Python applications, combining environment variable loading with validation and secret masking:
# config.py - Production-ready configuration management
from pydantic import SecretStr, Field, field_validator
from pydantic_settings import BaseSettings, SettingsConfigDict
class APISettings(BaseSettings):
"""Type-safe API configuration with automatic environment loading."""
model_config = SettingsConfigDict(
env_file=".env",
env_file_encoding="utf-8",
case_sensitive=False,
extra="ignore"
)
# Required secrets - will fail fast if missing
api_key: SecretStr = Field(..., description="Primary API key")
database_url: SecretStr = Field(..., description="Database connection string")
# Optional with defaults
api_base_url: str = "https://api.example.com/v1"
timeout_seconds: int = Field(default=30, ge=1, le=300)
max_retries: int = Field(default=3, ge=0, le=10)
debug: bool = False
@field_validator('api_base_url')
@classmethod
def validate_url(cls, v: str) -> str:
if not v.startswith(('http://', 'https://')):
raise ValueError('URL must start with http:// or https://')
return v.rstrip('/')
# Usage
settings = APISettings()
# SecretStr prevents accidental logging
print(settings.api_key) # Output: SecretStr('**********')
print(settings.api_key.get_secret_value()) # Actual value when needed
# Safe serialization excludes secrets
print(settings.model_dump()) # api_key shows as '**********'
✅ Why Pydantic Settings Over python-dotenv Alone
While python-dotenv handles .env file loading, Pydantic Settings adds type validation, required field enforcement, default values, secret masking in logs/dumps, and automatic conversion (strings to integers, booleans, etc.). The combination catches configuration errors at startup rather than runtime.
🚫 Anti-Pattern: Hardcoded Credentials
❌ DON’T
# This is in 40% of leaked credentials
API_KEY = "sk-proj-abc123..."
client = OpenAI(api_key=API_KEY)✅ DO
import os
from pydantic_settings import BaseSettings
class Settings(BaseSettings):
openai_api_key: SecretStr
settings = Settings()
client = OpenAI(
api_key=settings.openai_api_key.get_secret_value()
)4. Pagination Strategies for Scale
Pagination choice determines whether your API integration scales gracefully or collapses under load. The three primary approaches—offset, page-based, and cursor—each have distinct performance characteristics.
| Method | Performance | Consistency | Best For |
|---|---|---|---|
| Offset/Limit | O(n) – degrades with dataset size | ❌ Inconsistent if data changes | <10K records, static data |
| Page-Based | O(n) – same as offset | ❌ Same issues as offset | User-facing pagination |
| Cursor-Based | O(1) – constant time | ✅ Stable across changes | >10K records, real-time data |
Cursor Pagination Implementation
# Generic cursor pagination handler
from typing import Generator, Any
import httpx
def paginate_cursor(
client: httpx.Client,
base_url: str,
page_size: int = 100,
cursor_field: str = "next_cursor",
data_field: str = "data"
) -> Generator[list[Any], None, None]:
"""
Generic cursor pagination for APIs that return:
{"data": [...], "next_cursor": "abc123" | null}
"""
cursor = None
while True:
params = {"limit": page_size}
if cursor:
params["cursor"] = cursor
response = client.get(base_url, params=params)
response.raise_for_status()
payload = response.json()
data = payload.get(data_field, [])
if not data:
break
yield data
cursor = payload.get(cursor_field)
if not cursor:
break
# Usage
with httpx.Client(timeout=30.0) as client:
all_users = []
for page in paginate_cursor(client, "https://api.example.com/users"):
all_users.extend(page)
print(f"Fetched {len(all_users)} users so far...")
💡 Slack’s Cursor Encoding Pattern
APIs like Slack encode cursor data as base64 strings (e.g., dXNlcjpXMDdRQ1JQQTQ= “user:W07QCRPA4”). This obfuscation prevents clients from hard-coding cursor values, allowing the API to change pagination logic without breaking integrations. Treat cursors as opaque strings.
5. Error Handling Beyond Try/Except
Production API automation requires structured error handling that distinguishes between transient failures (retry) and permanent failures (escalate). The requests library provides specific exception types for this purpose:
# Comprehensive error handling hierarchy
import requests
from requests.exceptions import (
ConnectionError, # Network unreachable
Timeout, # Request timed out
HTTPError, # 4xx/5xx responses
TooManyRedirects, # Redirect loop
RequestException # Base class for all
)
def robust_api_call(url: str, max_retries: int = 3) -> dict | None:
"""
API call with differentiated error handling.
- Retries: ConnectionError, Timeout, 429, 5xx
- Fails fast: 4xx (except 429), TooManyRedirects
"""
retry_exceptions = (ConnectionError, Timeout)
retry_status_codes = {429, 500, 502, 503, 504}
for attempt in range(max_retries):
try:
response = requests.get(url, timeout=(3.05, 27))
if response.status_code in retry_status_codes:
delay = 2 ** attempt
if response.status_code == 429:
# Honor Retry-After if present
retry_after = response.headers.get('Retry-After')
if retry_after:
delay = max(float(retry_after), delay)
print(f"Status {response.status_code}, retrying in {delay}s")
time.sleep(delay)
continue
response.raise_for_status()
return response.json()
except retry_exceptions as e:
if attempt == max_retries - 1:
raise
delay = 2 ** attempt
print(f"Transient error: {e}. Retrying in {delay}s")
time.sleep(delay)
except HTTPError as e:
# 4xx errors (except 429) - don't retry
print(f"Client error: {e}")
raise
except TooManyRedirects:
print("Redirect loop detected")
raise
return None
Structured Logging for API Calls
# Structured logging for observability
import logging
import json
from datetime import datetime
logger = logging.getLogger(__name__)
def log_api_call(
method: str,
url: str,
status_code: int,
duration_ms: float,
success: bool,
error: str | None = None
):
"""Emit structured log for API observability."""
log_entry = {
"timestamp": datetime.utcnow().isoformat(),
"event": "api_call",
"method": method,
"url": url,
"status_code": status_code,
"duration_ms": round(duration_ms, 2),
"success": success,
}
if error:
log_entry["error"] = error
logger.info(json.dumps(log_entry))



6. Connection Pooling and Session Management
Each HTTP request without connection reuse incurs TCP handshake overhead (~50-100 ms) plus TLS negotiation (~100-300 ms). For APIs requiring multiple calls, connection pooling reduces this to near-zero for subsequent requests.
# Connection pooling with requests Session
import requests
from requests.adapters import HTTPAdapter
def create_session(
pool_connections: int = 10,
pool_maxsize: int = 10,
max_retries: int = 3
) -> requests.Session:
"""Create a session with connection pooling."""
session = requests.Session()
adapter = HTTPAdapter(
pool_connections=pool_connections,
pool_maxsize=pool_maxsize,
max_retries=max_retries
)
session.mount('https://', adapter)
session.mount('http://', adapter)
return session
# Use as context manager
with create_session() as session:
# All requests reuse connections
for i in range(100):
response = session.get(f"https://api.example.com/item/{i}")
⚠️ Connection Pool Sizing
pool_connections is the number of connection pools to cache (typically per host). pool_maxsize is the number of connections per pool. For most API clients hitting a single service, pool_connections=1 it pool_maxsize=10-20 is appropriate. Oversizing wastes memory; undersizing causes connection churn.
Common Myths Debunked
Myth 1: “Private Repos Keep Secrets Safe”
GitGuardian found that 35% of private repositories contain plaintext secrets. Private repos are 9× more likely to contain hardcoded credentials than public ones—developers are less cautious when code isn’t public. AWS IAM keys appear in 8% of private repositories.
Myth 2: “async is Always Faster.”
For sequential API calls with processing between each, async provides zero benefit. The overhead of the event loop can actually slow simple scripts. Async excels only when I/O operations can genuinely overlap—concurrent requests, parallel file operations, or mixed workloads.
Myth 3: “Rate Limits Mean the API is Poorly Designed”
Rate limits protect both the API provider and consumers. Without them, a single misbehaving client could degrade service for everyone. Production code should assume rate limits exist even when undocumented—and handle 429 responses gracefully.
Myth 4: “Environment Variables Are Secure”
Environment variables are readable by any process running as the same user. They appear /proc/*/environ on Linux and can leak through crash dumps, logging, and debugging tools. They’re better than hardcoding but not a substitute for proper secrets management in production.
🎯 Key Takeaways
- Default to requests for synchronous code; upgrade to httpx when you need async or HTTP/2
- Always implement exponential backoff with jitter—2-second base, 5 max retries, 50-150% randomization
- Use Pydantic Settings for configuration management—it validates, masks secrets, and fails fast
- Prefer cursor pagination for datasets over 10K records; offset pagination degrades at scale
- Honor Retry-After headers when present—they’re the server’s best estimate of recovery time
- Rotate API credentials quarterly at a minimum—70% of 2-year-old leaked secrets still work
- Use connection pooling via Session objects—40-60% latency reduction on repeated calls
- Log API calls with structured data—status codes, durations, and errors for observability
- Never use python-dotenv in production alone—add Pydantic Settings for validation
- Test pagination edge cases—empty pages, single-item pages, and concurrent modifications
Frequently Asked Questions
Q: Should I use requests or httpx for a new project in 2026?
Start with it requests unless you know you need async. It has better documentation, more Stack Overflow answers, and broader library compatibility. Upgrade to httpx when you hit performance limits or need HTTP/2. The APIs are similar enough that migration takes hours, not days.
Q: How do I handle APIs that don’t document their rate limits?
Implement defensive rate limiting anyway. Start conservative (1 request/second), monitor for 429s, and adjust. Use exponential backoff for any HTTP error. Some APIs silently throttle without 429s—watch for degraded response times.
Q: Is it safe to commit .env.example files with placeholder values?
Yes, if the placeholders are obviously fake (e.g., API_KEY=your-key-here). Never commit .env.example with real keys or realistic-looking test keys. GitGuardian scans example files too and will flag anything that looks like a real credential.
Q: What’s the right timeout value for API requests?
Use tuple timeouts: Connect timeout should be short (3-5 seconds)—if TCP can’t connect quickly, it won’t. Read timeout depends on the API; 30 seconds handles most cases. Never use timeout=None in production.
Q: How do I test rate-limited code without hitting real APIs?
Use responses (for requests) or respx (for httpx) to mock HTTP responses, including 429s. Libraries like pytest-httpx simplify async testing. Test the full retry sequence, including delays—mock time.sleep to avoid slow tests.
Q: Should I use aiohttp instead of httpx for maximum performance?
Only if benchmarks prove it matters for your use case. aiohttp can be 10× faster at extreme concurrency (300+ concurrent requests), but it’s async-only and has a steeper learning curve. For typical API integrations, httpx’s sync+async flexibility outweighs raw performance.
Q: How often should I rotate API credentials?
Quarterly minimum, monthly for high-value credentials (production databases, payment APIs). Immediately upon any suspicion of compromise. Automate rotation where possible—AWS Secrets Manager and HashiCorp Vault support automatic rotation for many services.
Q: What’s the best way to handle pagination when the API changes data between pages?
Cursor pagination handles this automatically—cursors point to specific records, not positions. For offset-based APIs with changing data, accept that you may see duplicates or miss records. Consider fetching all pages quickly to minimize the window for changes.
Q: Is there a maximum number of retries I should configure?
5 retries with exponential backoff is the typical maximum. With a 2-second base, that’s 2+4+8+16+32 = 62 seconds of delay. More retries rarely help—if 5 attempts over a minute fail, the issue is likely persistent. Log and alert instead of retrying forever.
Q: Should I use environment variables or a config file?
Both. Use environment variables for secrets and environment-specific settings (production vs. staging). Use config files for non-sensitive defaults that rarely change. Pydantic settings can load from both simultaneously, with clear precedence rules.
📝 Human-AI Collaboration Note: This guide integrates findings from automated research across multiple sources with practical patterns refined through production deployments. Code examples have been tested in Python 3.12 environments. Consider local testing before production deployment.
